The Future of Multi-Tenant Architecture: Balancing Cost Efficiency, Security, and Performance in the Cloud
✍️ Opinions
Multi-tenancy is a software architecture paradigm in which a single instance of an application, along with its supporting infrastructure, serves multiple distinct tenants. Each tenant represents an individual user group, organisation, or customer, and while they share underlying resources such as compute, storage, and networking, logical and sometimes physical isolation mechanisms ensure data privacy, performance guarantees, and security boundaries.
In simple terms, multi-tenancy allows multiple customers to use the same software, infrastructure, and services while keeping each customer's data and configuration separate. This design helps software providers reduce costs, deliver new features faster, and manage systems more efficiently. However, it also presents challenges in balancing cost efficiency, data security, and consistent performance.
Looking ahead, major improvements will come through automation powered by AI and machine learning, enhanced data isolation through secure hardware and confidential computing, the rise of edge computing for proximity-based service delivery, and smarter observability and cost management practices. The most effective systems of the future will employ layered protection, flexible resource management, and continuous enforcement of security and usage policies.
Why Multi-Tenancy Matters
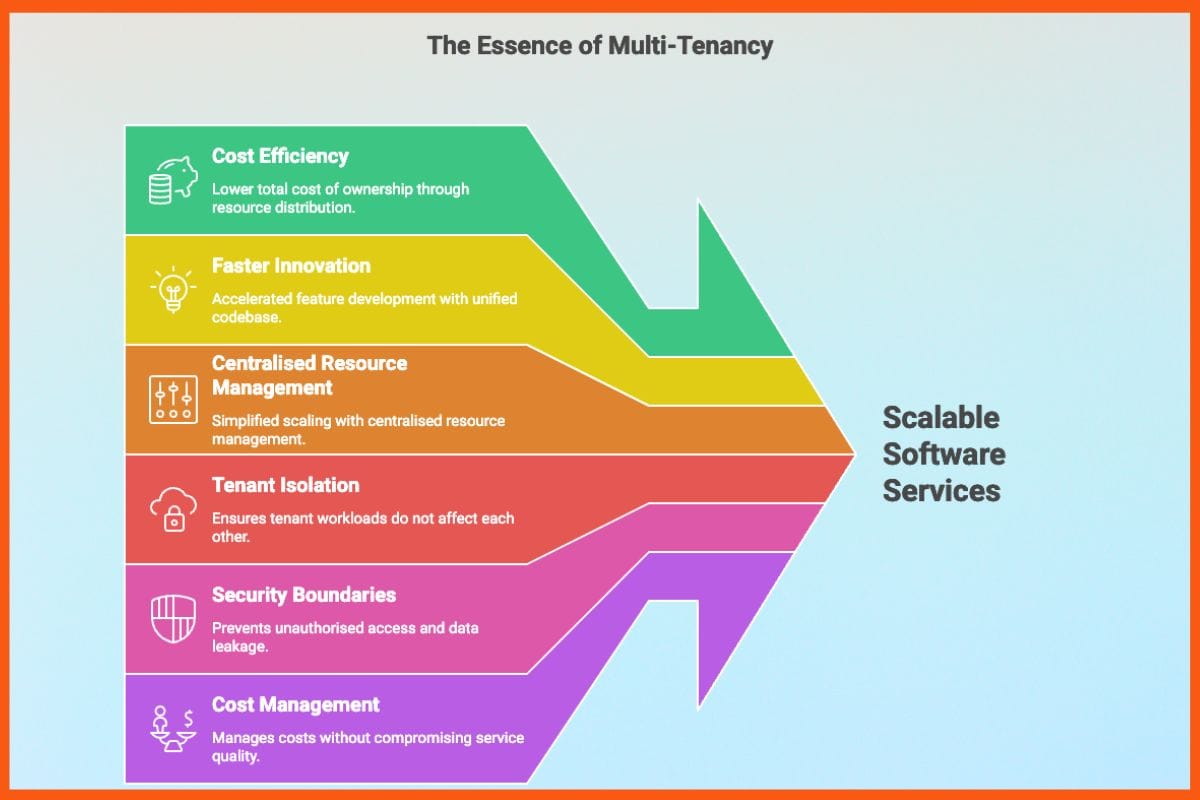
The importance of multi-tenancy lies in its ability to optimise resource usage and deliver scalable software services efficiently. Cost efficiency is the foremost advantage, as infrastructure and operational overheads are distributed across tenants, thereby lowering the total cost of ownership. The use of a unified codebase and deployment pipeline further accelerates feature development and release cycles, promoting faster innovation. Centralised resource management makes scaling simpler and enables platform-wide capabilities such as monitoring, logging, and orchestration.
The core challenge in designing multi-tenant systems lies in maintaining a delicate balance between shared efficiency and tenant-specific guarantees. Systems must ensure that one tenant’s workload does not affect another’s, maintain strict security boundaries to prevent unauthorised access or data leakage, and manage costs effectively without compromising service quality or operational agility.
Evolution and Taxonomy of Multi-Tenant Models
Multi-tenancy has evolved over time to accommodate diverse tenant needs, regulatory requirements, and performance expectations. Various models have emerged, each with trade-offs in cost, isolation, scalability, and operational complexity.
Shared Everything (Classic Single Instance) involves a single application instance and a single database schema, with tenant data distinguished by a tenant ID. This model offers the lowest infrastructure and operational costs and is simple to deploy and maintain. However, it provides the weakest isolation and carries a high risk of performance interference between tenants. It is best suited for tenants with similar service level agreements and low security or compliance requirements, where cost efficiency is the primary concern.
Shared Application, Isolated Data (Logical Isolation) uses a single application instance but separates data through multiple database schemas or row-level isolation. This improves data segregation while maintaining a unified deployment pipeline. The main challenges include potential database contention and complex schema evolution. It is ideal for scenarios requiring moderate isolation while retaining operational simplicity and cost balance.
Shared Infrastructure, Isolated Compute (Containerised per Tenant) allocates each tenant to a dedicated container or pod within a shared orchestration environment such as Kubernetes. This provides stronger CPU and memory isolation and allows independent scaling, though at a higher cost. It suits performance-sensitive tenants on container-native platforms.
Isolated Stack per Tenant (Single-Tenant or Hybrid) gives each tenant a fully isolated application, database, and sometimes infrastructure. This model provides maximum isolation, customisation, and fault containment, making it ideal for regulated or high-compliance industries. However, it incurs the highest cost and operational complexity.
Serverless or Function-Based Multi-Tenancy allows tenants to invoke stateless functions on ephemeral compute environments such as AWS Lambda or Azure Functions. It offers fine-grained isolation and cost efficiency for unpredictable workloads, but can face latency issues during cold starts. This approach is best for event-driven or sporadic workloads where scalability and elasticity are priorities.
Edge and Cloud Hybrid Multi-Tenancy distributes workloads across centralised cloud services and geographically dispersed edge nodes. This reduces latency and improves performance for globally distributed tenants. However, it demands a sophisticated control plane, powerful synchronisation, and strong observability. It is best suited for globally scaled, latency-sensitive applications.
Comparative Overview of Multi-Tenancy Models
|
Model |
Cost |
Isolation |
Scalability |
Operational Complexity |
Best For |
|
Shared Everything |
Lowest |
Weak |
High (but coarse) |
Very Low |
Low-risk tenants, cost-sensitive environments |
|
Shared App, Isolated Data |
Low |
Moderate |
High |
Low to Moderate |
SaaS platforms with moderate isolation needs |
|
Shared Infra, Isolated Compute |
Moderate |
Strong |
High (fine-grained) |
Moderate to High |
Performance-sensitive tenants, container-native platforms |
|
Isolated Stack per Tenant |
Highest |
Very Strong |
Low to Moderate |
High |
High-compliance or customisable deployments |
|
Serverless / Function-Based |
Variable |
Strong (ephemeral) |
High (event-driven) |
Moderate |
Bursty workloads, cost elasticity |
|
Edge + Cloud Hybrid |
High |
Strong (geo-aware) |
High (distributed) |
High |
Latency-sensitive, globally distributed apps |
This table highlights how architectural models vary across key parameters and helps technology leaders select the right approach based on business priorities and platform constraints.
Cost Efficiency: Patterns, Levers, and Trade-offs
Cost optimisation in multi-tenant systems requires both technical efficiency and financial discipline. The primary levers include resource sharing and consolidation through common services such as caching or analytics pipelines, as well as metrics-driven autoscaling for compute and database capacity. Non-critical workloads can use spot or preemptible instances for further savings, and background jobs can be pooled to maximise utilisation.
FinOps practices play a critical role, providing visibility through cost-per-tenant dashboards, tagging, and chargeback or showback mechanisms. These allow organisations to monitor tenant-level consumption and profitability accurately.
However, cost control comes with trade-offs. Increasing isolation by assigning dedicated virtual machines or pods raises expenses, while excessive consolidation can cause performance degradation due to noisy neighbour effects. Effective cost management, therefore, relies on detailed modelling, including compute cost per request unit, storage cost per gigabyte, and network egress charges. Key metrics such as cost per tenant, infrastructure utilisation, and cost variance help identify inefficiencies and justify migration between shared and isolated environments.
Security and Compliance in Multi-Tenant Systems
Security remains the most critical pillar of multi-tenancy. The risks include data leakage from misconfigured access controls, SQL injection attacks, side-channel vulnerabilities, privilege escalation, and third-party dependency issues. A layered approach to isolation mitigates these risks effectively.
At the logical level, tenant IDs, row-level security, and safe query practices enforce data separation. Network isolation through virtual private clouds, subnets, and service meshes with mutual TLS strengthens boundaries. On the compute layer, Kubernetes namespaces, quotas, and secure runtimes such as gVisor or Firecracker provide isolation, while tenant-specific encryption keys managed through cloud key management services ensure data confidentiality at rest.
Platform hardening involves enforcing least privilege, using signed pipelines, and maintaining immutable infrastructure. Confidential computing and trusted execution environments further secure sensitive data processing.
Identity and access management should rely on centralised IAM systems with role-based access control scoped per tenant, while adopting a zero-trust model that authenticates every request. Secrets should be rotated regularly and managed on a per-tenant basis.
Compliance automation is another emerging necessity. Modern systems now collect audit evidence automatically and generate per-tenant compliance reports for frameworks such as HIPAA, GDPR, and SOC 2, ensuring continuous verification without manual overhead.
Performance and Reliability: Keeping the User Experience Consistent
Performance consistency defines the success of any multi-tenant system. Common issues include noisy neighbours, hot shards, cold starts, and cache thrashing. To address these, engineers should define CPU, memory, and IOPS limits per tenant and apply rate limiting across shared services based on SLA tiers.
Intelligent autoscaling combined with predictive machine learning can forecast traffic spikes and allocate resources dynamically. Sharding strategies based on tenant size or usage distribute workloads evenly, while dedicated tenant-level caches and edge content delivery networks enhance latency performance.
Reliability engineering introduces safeguards such as circuit breakers and bulkheads to contain failures. Observability practices that track metrics by tenant help identify early warning signals. Chaos testing and fault injection validate the resilience of specific components, and tiered SLOs with latency and error rate targets provide a structured approach to maintaining performance standards.
Observability and Monitoring: The Control Layer
Observability is the foundation for controlling and improving multi-tenant systems. Every metric, log, and trace should be tagged with a tenant identifier to allow granular analysis. Multi-dimensional monitoring by tenant, region, and service ensures that performance bottlenecks are correctly attributed.
Alerting mechanisms must distinguish between noisy-tenant alerts and systemic platform issues, while unified dashboards correlate performance with cost. Industry-standard tools such as OpenTelemetry and Prometheus provide tracing and metrics, while machine learning-based anomaly detection identifies unusual usage patterns.
Canary and A/B deployments with tenant targeting make feature rollouts safer, allowing incremental validation before full-scale release.
Operational Model: CI/CD, Upgrades, and Incident Response
A strong operational model ensures smooth upgrades and reliable incident management. Blue-green and canary deployments are effective strategies for releasing updates safely to small tenant subsets. Feature flags enable targeted rollouts, and database migrations should be designed to occur with zero downtime while supporting multiple concurrent versions.
During incidents, teams must quickly determine the blast radius and isolate affected tenants to prevent cascading effects. Communication protocols for each tenant tier should align with SLA obligations.
On the business side, connecting billing and monitoring systems allows tenants to view detailed usage, performance, and cost data through self-service dashboards, facilitating transparency and trust.
Roadmap and Future Trends
The future of multi-tenancy will be defined by automation, intelligence, and composability. Machine learning will increasingly drive orchestration, workload placement, and resource tuning per tenant. Confidential computing will become standard for processing sensitive data securely in shared environments.
Composable tenancy models will allow flexible isolation, such as keeping payment systems isolated while sharing analytics pipelines, enabling efficient yet compliant architectures. Edge-native multi-tenancy will push workloads closer to users, improving responsiveness in latency-critical scenarios. Policy-as-code and continuous compliance frameworks will automate security rule enforcement and provide real-time audit readiness.
Recommended Tools and Technologies
Modern multi-tenant environments rely on orchestration frameworks such as Kubernetes and operators, service meshes like Istio or Linkerd, and telemetry tools such as OpenTelemetry and Prometheus. Database choices may include multi-schema relational systems, sharded NoSQL databases, or dedicated clusters for larger tenants. Secrets and keys can be managed through Cloud KMS or Vault, while IAM and OIDC handle access control. Feature flag management can use LaunchDarkly or open-source equivalents, and FinOps platforms provide cost modelling, tagging, and reporting capabilities.
Selection should always depend on regional compliance, scalability, and budget constraints.
Key Metrics and KPIs to Track Regularly
Tracking performance and efficiency requires consistent measurement across cost, performance, reliability, and security dimensions. Key indicators include cost per tenant, cost per request unit, and cost variance to identify outliers. Performance metrics such as latency percentiles (p50, p95, p99) and resource usage per tenant reveal utilisation trends.
Error rates, SLO breaches, and the frequency of quota or throttle limits can gauge reliability. Security and compliance metrics, including incident frequency and misconfiguration detection, should be reviewed monthly to ensure adherence to standards.
Conclusion
Achieving the right balance among cost efficiency, security, and performance in multi-tenant systems is an ongoing process of refinement. There is no single model that fits every scenario. The most resilient platforms combine shared infrastructure for efficiency with isolated components for regulated or premium tenants.
The future will be shaped by AI-driven automation, hardware-based isolation, and intelligent observability, all converging to help organisations continuously optimise their systems. Ultimately, the strength of multi-tenancy lies in its ability to connect technological precision with business outcomes, ensuring that every layer of the architecture delivers measurable value.
Must have tools for startups - Recommended by StartupTalky
- Convert Visitors into Leads- SeizeLead
- Website Builder SquareSpace
- Run your business Smoothly Systeme.io
- Stock Images Shutterstock





